Maintaining Software by Using Software Update Services
In this section, you will learn:
- How to install and configure SUS
- Managing an SUS infrastructure
- Designing your SUS infrastructure
- Configuring clients for SUS
Introduction to Software Update Services
Security and patch management is an essential part of systems administration in a Microsoft Windows environment. With security risk and holes appearing almost daily, keeping your enterprise up to date with patch management is essential.
With Microsoft Windows Server 2003, you can lower your costs and downtime by implementing Software Update Services (SUS). SUS is a free, automated and flexible software patch management solution for your enterprise.
SUS allows administrator control by scheduling when an update is installed and allows administrators to approve updates prior to installing them. SUS leverages the Automatic Updates feature of Windows 2000 and newer – NT and older machines do not participate in the SUS infrastructure.
SUS delivers these updates within the corporate network – the clients do not require Internet access. In addition, you can tier the servers to serve thousands of clients and have update servers close to the end user.
Installing and Configuring SUS
SUS is a free add on product for Windows Server 2003 (and for Window 2000 Server). It can be downloaded from Microsoft.com. You can download SUS from: http://www.microsoft.com/windowsserversystem/sus/
The primary requirement for installing SUS is you must have Internet Information Services (IIS) installed on the server. SUS integrates into IIS and uses a lot of its functionality to deliver updates.
If you have not yet installed IIS, you can do so by:
- Open the Control Panel and choose Add or Remove Programs.
- Click Add/Remove Windows Components.
- Click Application Server and choose Details.
- Check the box next to Internet Information Services (IIS). Click OK.
- Click Next.
- The server will begin copying the required files and will begin installing IIS. Click Finish when it has completed.
- Close the Add or Remove Programs control panel.
Once you have installed IIS, open the setup program for Software Update Services.
- Click Next.
- Click I accept the terms in the License Agreement.
- Click Next.
- Click Typical.
- It will provide you the address for users to download updates.
- Click Install.
- Click Finish.
Managing an SUS infrastructure
Checking for vulnerabilities
Microsoft provides a free utility, Microsoft Baseline Security Analyzer, which will allow you to scan your environment for a number of security hazards. MSBA can be installed in Windows XP, Windows 2000, and Windows Server 2003 and enables users to scan one or more computers for missing security updates and common security misconfigurations.
Microsoft Baseline Security Analyzer can be downloaded from http://www.microsoft.com/technet/security/tools/mbsahome.mspx
Designing Your SUS Infrastructure
SUS is designed to allow you flexibility in the design of your patch updates environment. SUS can receive its package updates from internal servers or directly from Microsoft. With this design, you could design your infrastructure in a variety of ways. The two most common layouts are:
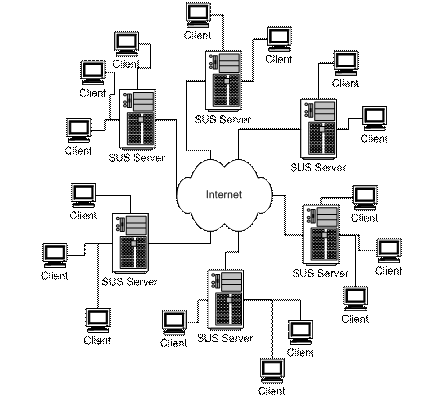
With this layout, each SUS server connects to Microsoft for its updates. Each one is administered individually. This layout is ideal where a company has many locations with no centralized IT support.

In larger companies, this infrastructure is more common. A central SUS server connects to Microsoft for updates and the approval of th
e updates is controlled by an administrator. The other SUS servers in the network connect to the central server for updates and deploy out to clients.
Some companies choose a hybrid model where some servers are tiered behind a central SUS server and other SUS servers connect directly to Microsoft for updates. This is commonly used when remote locations have their own Internet connections – reducing the bandwidth to the corporate office.
Client Support
Configuring clients for SUS can be a manual task or you can deploy it through Group Policy.
- Open Group Policy Object Editor for the Group Policy you want to edit.
- Navigate to Computer Configuration: Administrative Templates: Windows Components: Windows Update.
- There are four options available:

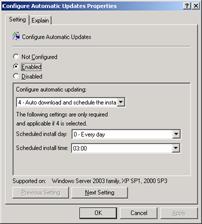
Configure Automatic Updates – When you enable this setting, it turns automatic updates on for the client. You can set whether or not to automatically install updates and what time to install them.

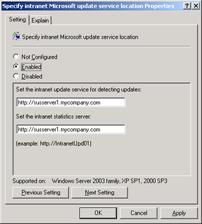
Specify intranet Microsoft update service location – By enabling this setting, you allow the client to receive its update from an internal SUS server instead of directly from Microsoft. You must the set the name of the SUS server and the name of the stats server (can be the same server).

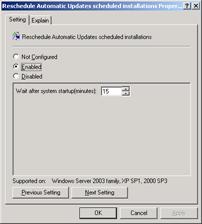
Reschedule Automatic Updates scheduled installations – sets the amount of time after bootup that Automatic Updates installs updates if the computer missed the standard update time.

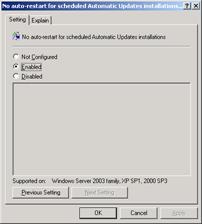
No auto-restart for scheduled Automatic Updates installations – you can set the client to not reboot the machine after updates install. The user would need to manually reboot the machine after updating if you enable this setting. - Once you have changed the settings, close Group Policy Object Editor.
You can also deploy the SUS settings manually to machines not affected by Group Policy. To deploy it manually, create a LoadSUS.reg file with these contents:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU]
“RescheduleWaitTime”=dword:00000004
“NoAutoRebootWithLoggedOnUsers”=dword:00000001
“NoAutoUpdate”=dword:00000000
“AUOptions”=dword:00000004
“ScheduledInstallDay”=dword:00000000
“ScheduledInstallTime”=dword:00000003
“UseWUServer”=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate]
“WUServer”=”http://susserver1.mycompany.com/”
“WUStatusServer”=”http://susserver1.mycompany.com/”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update]
“AUState”=dword:00000002
These settings mirror the settings above in Group Policy. You can find more information in the SUS white paper at: http://www.microsoft.com/windowsserversystem/sus/susdeployment.mspx