Basic Active Directory Components
At its core, Active Directory needs structure to work properly. It provides the basic building blocks for people to build their own directory. These basic building blocks of Active Directory include domains, domain controllers, trusts, forests, organizational units, groups, sites, replication, and the global catalog.
Understanding Forests
At the top of the Active Directory structure is a forest. A forest holds all of the objects, organizational units, domains, and attributes in its hierarchy. Under a forest are one or more trees which hold domains, OUs, objects, and attributes.
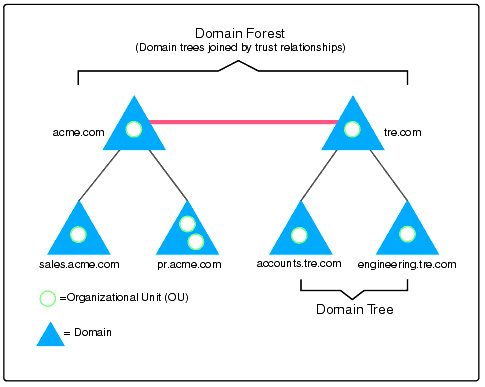
As illustrated in this image, there are two trees in the forest. You might use a structure like this for
organizations with more than one operating company.
You could also design a structure with multiple forests, but these are for very specific reasons and not common.
Domains
At the heart of the Active Directory structure is the domain. The domain is typically of the Internet naming variety (e.g. Learnthat.com), but you are not forced to stick with this structure – you could technically name your domain whatever you wish.
Microsoft recommends using as few domains and possible in building your Active Directory structure and to rely on Organizational Units for structure. Domains can contain multiple nested OUs, allowing you to build a pretty robust and specific structure.
Domain Controllers
In Windows NT, domains used a Primary Domain Controller (PDC) and Backup Domain Controller (BDC) model. This had one server, the PDC, which was “in charge” while the other DCs where subservient. If the PDC failed, you had to promote a BDC to become the PDC and be the server in charge.
In Active Directory, you have multiple Domain Controllers which are equal peers. Each DC in the Active Directory domain contains a copy of the AD database and synchronizes changes with all other DCs by multi-master replication. Replication occurs frequently and on a pull basis instead of a push one. A server requests updates from a fellow domain controller. If information on one DC changes (e.g. a user changes their password), it sends signal to the other domain controllers to begin a pull replication of the data to ensure they are all up to date.
Servers not serving as DCs, but in the Active Directory domain, are called ‘member servers.’
Active Directory requires at least one Domain Controller, but you can install as many as you want (and it’s recommended you install at least two domain controllers in case one fails).
Trust Relationships
Trust Relationships are important in an Active Directory environment so forests and domains can communicate with one another and pass credentials. Within a single forest, trusts are created when a domain is created. By default, domains have an implicit two-way transitive trust created. This means each domain trusts each other for security access and credentials. A user in domain A can access resources permitted to him in domain B while a user in domain B can access resources permitted to her in domain A.
AD allows several different types of trusts to be created, but understanding the two-way transitive trust is the most important to understanding AD.
Organizational Units
An Organizational Unit (OU) is a container which gives a domain hierarchy and structure. It is used for ease of administration and to create an AD structure in the company’s geographic or organizational terms.
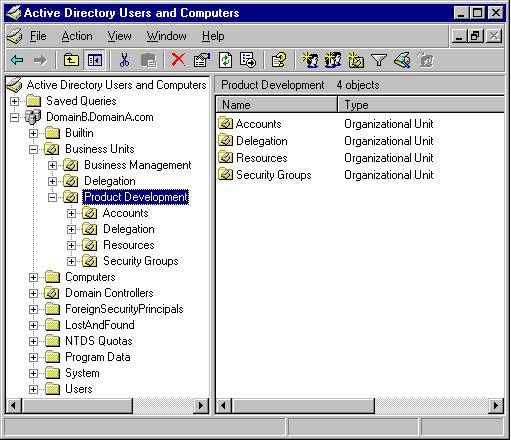
Organizational Units
An OU can contain OUs, allowing for the creating of a multi-level structure, as shown in the image above. There are three primary reasons for creating OUs:
Organizational Structure: First, creating OUs allows a company to build a structure in Active Directory which matches their firm’s geographic or organizational structure. This permits ease of administration and a clean structure.
Security Rights: The second reason to create an OU structure is to assign security rights to certain OUs. This, for example, would allow you to apply Active Directory Policies to one OU which are different than another. You could setup policies which install an accounting software application on computers in the Accounting OU.
Delegated Administration: The third reason to create OUs is to delegate administrative responsibility. AD Architects can design the structure to allow local administrators certain administrative responsibility for their OU and no other. This allows for a delegated administration not available in Windows NT networks.
Groups
Groups serve two functions in Active Directory: security and distribution.
A security group contains accounts which can be used for security access. For example, a security group could be assigned rights to a particular directory on a file server.
A distribution group is used for sending information to users. It cannot be used for security access.
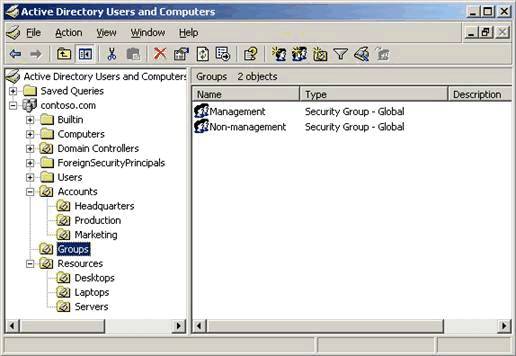
There are three group scopes:
Global: Global scope security groups contains users only from the domain in which is created. Global security groups can be members of both Universal and Domain Local groups.
Universal: Universal scope security groups can contain users, global groups, and universal groups from any domain. These groups are typically used in a multi-domain environment if access is required across domains.
Domain Local: Domain Local scope groups are often created in domains to assign security access to a particular local domain resource. Domain Local scope groups can contain user accounts, universal groups, and global groups from any domain. Domain Local scope groups can contain domain local groups in the same domain.
Sites
An Active Directory site object represents a collection of IP subnets, usually constituting a physical Local Area Network (LAN). Multiple sites are connected for replication by site links. Typically, sites are used for:
Physical Location Determination: Enables clients to find local resources such as printers, shares, or domain controllers.
Replication: You can optimize replication between domain controllers by creating links.
By default, Active Directory uses automatic site coverage, though you can purposefully setup sites and resources.
Replication
Since most Active Directory networks contain multiple domain controllers and users could theoretically attach to any DC for authentication or information, each of the servers needs to be kept up to date. Domain Controllers stay up to date by replicating the database between each other. It performs this using a pull method – a server requests new information from a different DC frequently. After a change, the DC initiates a replication after waiting 15 seconds (in Windows 2003) or 5 minutes (in Windows 2000). Windows Server 2003 uses technology to only replicate changed information and compressions replication over WAN links.
Windows Server sets up a replication topology to determine where a server updates from. In a large network, this keeps replication time down as servers replicate in a form of a ring network.
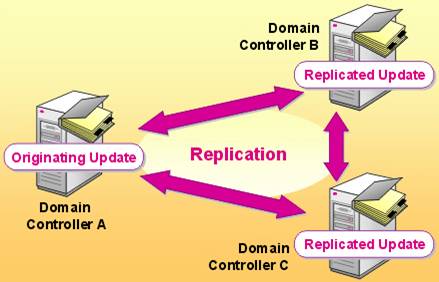
Active Directory uses multi-master replication. Multimaster replication does not rely on a single primary domain controller, but instead treats each DC as an authority. When a change is made on any DC, it is replicated to all other DCs. Although each DC is replicated alike, all of the DCs aren’t equal. There are several flexible single-master operation roles which are assigned to one domain controller at a time.
AD uses Remote Procedure Calls (RPC) for replication and can use SMTP for changes to schema or configuration.
FSMO Roles
All domain controll
ers are not equal. We know, it’s hard to hear. You’ve spent this whole time reading this tutorial thinking that all DCs are created equal and now we have to burst your bubble. Some DCs have more responsibility than others. It’s just part of life!
There are five roles which are called operations masters, or flexible single-master operations (FSMOs). Two are forestwide roles and three are domainwide roles. The forestwide roles are:
Schema master: Controls update to the Active Directory schema.
Domain naming master: Controls the addition and removal of domains from the forest.
The three domainwide roles are:
RID master: Allocates pools of unique identifier to domain controllers for use when creating objects. (RID is relative identifier).
Infrastructure master: Synchronizes cross-domain group membership changes. The infrastructure master cannot run on a global catalog server, unless all of the DCs are global catalog servers.
PDC Emulator: Provides backward compatibility for NT 4 clients for PDC operations – such as a password change. The PDC also serves as the master time server.
Global Catalog
As a network gets larger, it can contain multiple domains and many domain controllers. Each domain only contains records from its own domain in its AD database to keep the database small and replication manageable. The Active Directory domain relies on a global catalog database which contains a global listing of all objects in the forest. The Global Catalog is held on DCs configured as global catalog servers.
The global catalog contains a subset of information – such as a user’s first name and last name – and the distinguished name of the object so your client can contact the proper domain controller if you need more information. The distinguished name is the full address of an object in the directory. For example, a printer in the OU Accounting in the Learnthat.com domain might have a distinguished name of:
CN=AcctLaser1,OU=Accounting,DC=Learnthat,DC=com
The GC database is only a subset of the entire database called the Partial Attribute Set (PAS), containing 151 of the 1,070 properties available in Windows Server 2003. You can define additional properties for replication to the GC by modifying schema.

