Implementing Group Policy
In this section, you will learn:
- What Group Policy is
- Recommended Group Policy settings
- Implementing Group Policy objects
Group Policy was probably the most significant change for Microsoft with the release of Windows 2000 Server. Group Policy allows you to define settings and configurations to machines and groups of users. An administrator can use Group Policy to set policies at a site, domain, or organizational unit. Group Policy is supported in Windows 2000 Professional and newer operating systems.
Group Policy was designed to allow you to easily control the settings and configuration of a lot of machines, reducing your total cost of ownership. It is a very powerful part of the Active Directory, and if implemented correctly, can save you money. If it is not implemented correctly, it can cost your organization time and resources – fixing what can be huge mistakes!
Group Policy allows you to define user related policies, as well as network settings, security settings, and machine policies. In addition, you can use Group Policy to manage settings on your servers.
Group Policy was improved with the release of Windows Server 2003. There were hundreds of new policies added, as well as a new Group Policy Management Console. We will assume you have this installed throughout this tutorial. If you do not currently have it, please visit http://www.microsoft.com/windowsserver2003/gpmc/ to download GPMC.
Group Policy is different from policies used in Windows NT 4 domains. Group Policy is much more powerful, allows for more flexibility, and is easier to administer.
Implementing Group Policy is not a simple task so you should plan your implementation very carefully. If you turn on the wrong policy, you can mistakenly prevent your users from accessing the network (we know one small business administrator who did this) or prevent an entire business unit from opening Microsoft Outlook (we know one large enterprise administrator who did this). Group Policy is very powerful and should be configured with a great level of planning and discussion.
If you plan on using Group Policy settings (which you should to make your workstation administration easier), we recommend reviewing all of the Group Policy settings as a team with your network administrators, help desk, and PC support groups. This is a long process and can drag out, but we will highlight some of the Group Policy settings you may want to make and the reason we suggest them.
Recommended Group Policy Settings
This is by no means a definitive list. We will make some recommendations to you for your Group Policy settings. This could be considered a starter list. You should review all of the Group Policy settings to see how they fit in your business requirements.
There are three categories of group policy settings underneath two broad groups: Computer Configuration and User Configuration. Inside those are Software Settings, Windows Settings, and Administrative Templates.
Policies you apply within Computer Configuration apply to the whole computer (and all of its users) while settings you apply within User Configuration apply to a the specific user.
We are offering these as recommendations. You should review all group policy changes prior to implementation.
Computer Configuration: Windows Settings: Security Settings: Account Policies: Password Policy
Group Policy Objects to Set: Enforce password history; maximum password age; minimum password age, minimum password length; Password must meet complexity requirements.
By default, these policy objects are set. In our environment, password history is set to ‘6 passwords remembered’; maximum password age is set at 45 days; and minimum password length is set to 7 characters.
There are frequent questions surrounding the minimum password age of ‘1 day’ and why it is important to have a minimum password age. If a user is forced to change their password every 42 days (as in the default policy), the user could simply change their password the required number of times to get back to their original password. To prevent this security issue, a minimum password age is set so the user can only change their passwords once a day.
Computer Configuration: Windows Settings: Security Settings: Account Policies: Account Lockout Policy
There are three policy settings in this category: account lockout duration; account lockout threshold; reset account lockout counter after. We recommend setting the Account lockout threshold to ‘5 invalid login attempts.’ This will automatically set the other two settings to 30 minutes.
This setting will lock a user account for 30 minutes if there are five invalid login attempts. This helps stop hackers from using automated password guessing software on user accounts.
Computer Configuration: Windows Settings: Security Settings: Local Policies: Audit Policy
There are several security items you can audit under the audit policy. To audit in Windows means to record the actions in the local logs. We recommend you audit the successes and failures of: account logon events, account management, logon events, policy change, and privilege use. We recommend you audit the failures of the rest of the items.
Computer Configuration: Windows Settings: Security Settings: Local Policies: Security Options
We recommend you set Accounts: Rename administrator account to enabled and rename the administrator account to something else. This will help increase security by not giving a potential hacker the username at the start.
You should also consider setting Interactive logon: Do not display last user name to Enabled. This will display a blank username field at every boot – the user will be responsible for remembering their username. If someone gains access to the workstation physically, they would need to know a username to attempt to login.
Computer Configuration: Administrative Templates: Windows Components
The Administrative Templates section of Group Policy allows you to set policies for the Windows operating system and its components.
Computer Configuration: Administrative Templates: Windows Components: Internet Explorer
If you have a proxy or ISA server, you may want to set Make proxy settings per-machine. This policy will allow you to set the policy settings for one account and then every account that logs in will receive the proxy settings.
Computer Configuration: Administrative Templates: Windows Components: Internet Information Services
If you set Prevent IIS installation, you can prevent rogue IIS servers from popping up on the network.
Computer Configuration: Administrative Templates: Windows Components: Windows Messenger
We do not like the Windows Messenger (the MSN like instant messenger application Microsoft installs by default). We enable Do not allow Windows Messenger to be run and Do not automatically start Windows Messenger initially.
Computer Configuration: Administrative Templates: Windows Components: Windows Update
If you are using SUS or want the machines to perform automatic updates, you can configure those options in this section.
User Configuration: Windows Settings: Internet Explorer Maintenance
There are several configuration options for Internet Explorer. If you want to force users to have the same homepage or options, you can configure these options.
There are hundreds of policy settings you could potentially apply. We recommend caution and to only apply policies that are absolutely necessary – leaving the rest as “Not Configured.” This will make your user community much happier.
Implementing Group Policy Objects
Group Policy Objects are linked to Active Directory containers: sites, domains, or organizational units. GPOs cannot be linked directly to users, computers, or security groups.
GPOs can be linked to multiple sites, domains, or organizational units. In addition, a site, domain, or organizational unit can be linked to several GPOs.
When you link multiple GPOs to a single container (domain, site, or OU), you can specify the order in which the Group Policy Objects are processed. The lowest link order GPO in the list has the highest precedence and overwrites the settings of all other GPOs.
Group Policy is processed in this order:
- Local GPO – each computer has a local GPO which is processed first.
- Site – GPOs linked to a site that a computer belongs to are processed next. If multiple GPOs are linked to a site, the lowest link order GPO (e.g., the first GPO) is processed last, or has the highest precedence over the other GPOs.
- Domain – GPOs linked to the domain are processed next. Like with the Site GPOs, the ones which have the lowest link order (e.g. link #1) are processed last. They overwrite any settings applied by other GPOs before it.
- Organizational Units – GPOs are then processed on the OUs. The highest OU in the AD hierarchy is processed first, then its child OUs, until it reaches the OU which the computer or user is in. These OUs are processed last and have the highest priority over any other settings made before it.
You can view the precedence of Group Policies on any site, domain, or OU by clicking on the Group Policy Inheritance tab. This lists all of the Group Policy Objects that affect that unit in AD in order of precedence. The policy at the top of the list – in the #1 slot – applies last and takes precedence over all of the other GPOs linked throughout the hierarchy for that site, domain, or Organizational Unit.
Implementing Group Policy on a Organizational Unit
As an example, we are going to implement a Group Policy on an Organizational Unit in Active Directory. The first part of the process is to create a Group Policy Object for an Organizational Unit. You can create this on the actual OU or just create it in the Group Policy Objects container and then apply it to an OU, site, or domain later.
- Open the Group Policy Management snap-in.
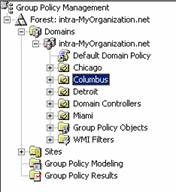
- Open the Forest and Domain.
- Right-click on Group Policy Objects and select New.
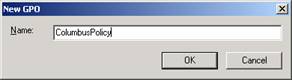
- Name your policy and click OK.
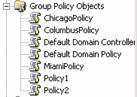
- If you open Group Policy Objects, you will see the new policy you created.
Now we are going to link a GPO to an Organizational Unit.
![]()
- Click on Link an Existing GPO to link the GPO you just created to the OU.
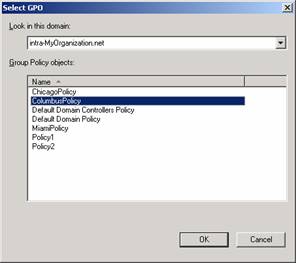
- Select the Group Policy Object you want to link. Click OK.

- You will now see the GPO linked in the view of the OU.
- You can edit the GPO by right-clicking on it and selecting Edit.

